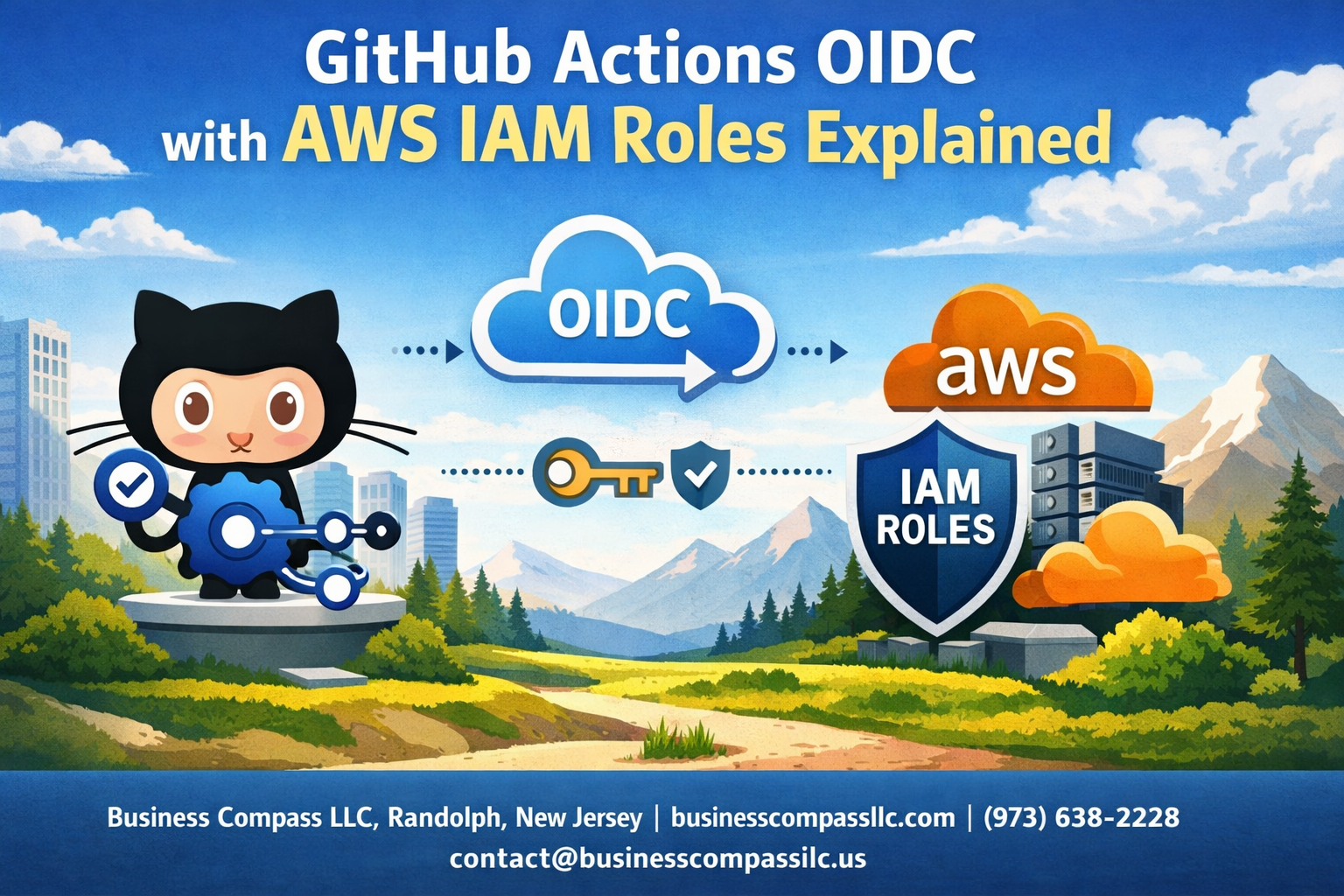
GitHub Actions OIDC AWS integration eliminates the need to store long-lived AWS credentials in your repositories, making your CI/CD pipelines more secure and easier to manage. This guide is for DevOps engineers, cloud architects, and developers who want to set up secure, keyless authentication between their GitHub workflows and AWS resources using OpenID Connect AWS IAM roles.
You’ll learn how GitHub Actions AWS authentication works through OIDC, replacing static access keys with temporary, scoped tokens that AWS generates on demand. We’ll walk through the complete GitHub Actions OIDC configuration process, from creating your OIDC provider AWS setup to implementing the authentication flow in your workflows.
Finally, we’ll cover practical troubleshooting steps for common integration issues, so you can confidently deploy your GitHub Actions secure deployment pipeline without the headaches of credential management or permission errors.
Understanding OpenID Connect for Secure Authentication

What is OIDC and how it eliminates long-lived credentials
OpenID Connect (OIDC) is an identity layer built on top of OAuth 2.0 that enables applications to verify user identities without storing permanent credentials. In the context of GitHub Actions AWS integration, OIDC works as a bridge between GitHub’s identity provider and AWS IAM roles, creating temporary authentication tokens instead of relying on static access keys.
Traditional authentication methods require storing AWS access keys and secret keys as GitHub secrets, creating security vulnerabilities. These long-lived credentials never expire automatically and can be compromised if repositories are breached or secrets are inadvertently exposed. OIDC solves this problem by generating short-lived tokens that are automatically issued when workflows run.
When GitHub Actions workflows execute, they request an identity token from GitHub’s OIDC provider. This token contains metadata about the workflow, repository, and execution context. AWS then validates this token against configured trust policies and issues temporary credentials with specific permissions. The entire process happens dynamically without any permanent secrets stored in your repository.
The OIDC tokens typically expire within minutes or hours, drastically reducing the attack surface. Even if a token is intercepted, its limited lifespan and scope-specific permissions minimize potential damage. This approach aligns with security best practices of principle of least privilege and just-in-time access.
Benefits of token-based authentication over static keys
Token-based authentication through GitHub Actions OIDC AWS integration offers significant security improvements over traditional static key management. Static AWS access keys pose several risks: they don’t expire automatically, can be accidentally committed to version control, and provide persistent access that attackers can exploit indefinitely.
OIDC tokens eliminate these concerns through several key advantages:
- Automatic expiration: Tokens have built-in expiration times, typically ranging from 15 minutes to 1 hour
- Dynamic generation: Fresh tokens are created for each workflow execution
- Contextual information: Tokens include specific details about the repository, branch, and workflow trigger
- Auditable access: Each token request is logged and traceable
- Reduced secret sprawl: No need to manage and rotate multiple access keys across different repositories
The operational benefits are equally compelling. Teams no longer need to worry about key rotation schedules or updating secrets across multiple repositories when credentials change. GitHub Actions OIDC configuration automatically handles the token lifecycle, reducing maintenance overhead and human error.
Security teams gain better visibility into access patterns since each authentication event is tied to specific workflow executions. This granular tracking makes it easier to audit permissions and identify unusual access patterns that might indicate security issues.
OIDC identity providers and trust relationships
OIDC identity providers act as trusted third parties that issue and validate identity tokens. GitHub serves as an OIDC provider, creating a secure communication channel with AWS IAM through established trust relationships. This relationship allows AWS to verify that incoming requests genuinely originate from authorized GitHub repositories and workflows.
Trust relationships in GitHub Actions AWS IAM roles are defined through IAM role trust policies that specify conditions for accepting OIDC tokens. These policies can include restrictions based on:
- Repository ownership: Only specific GitHub organizations or users
- Branch protection: Limiting access to main or protected branches
- Workflow context: Restricting based on workflow names or trigger events
- Time constraints: Adding time-based access windows
The trust relationship configuration requires careful planning to balance security with operational flexibility. Too restrictive policies might block legitimate workflows, while overly permissive settings could create security gaps. Best practices include starting with narrow permissions and gradually expanding based on actual usage patterns.
AWS validates incoming OIDC tokens against the configured trust policy before issuing temporary credentials. This validation process checks the token signature, expiration, and claim values against the specified conditions. Only tokens that meet all criteria receive access to the requested AWS resources, ensuring that unauthorized access attempts are automatically rejected.
AWS IAM Roles and Their Security Advantages

How IAM roles provide temporary credentials
AWS IAM roles work differently from traditional access keys by providing temporary, time-limited credentials instead of permanent ones. When GitHub Actions OIDC AWS authentication occurs, the role generates short-lived security tokens that automatically expire after a specified duration, typically ranging from 15 minutes to 12 hours. These temporary credentials include an access key ID, secret access key, and session token that together grant the necessary permissions for your GitHub workflows.
The temporary nature of these credentials adds a significant security layer. Even if someone intercepts the credentials, they become useless once expired. The AWS Security Token Service (STS) handles this token generation and management automatically, ensuring your GitHub Actions AWS IAM roles integration remains secure without requiring manual intervention.
Cross-account access without permanent keys
Traditional AWS authentication methods often require storing permanent access keys as secrets in your GitHub repository. This approach creates several security risks – keys can be accidentally exposed in logs, compromised through data breaches, or misused if not properly rotated. GitHub Actions AWS authentication using OIDC eliminates these risks entirely.
With OIDC provider AWS setup, you can grant cross-account access without embedding any permanent credentials in your workflows. Your GitHub repository can assume roles in multiple AWS accounts based on configurable trust policies. This means a single GitHub Actions workflow can deploy resources to development, staging, and production accounts without managing separate sets of access keys for each environment.
Fine-grained permissions and least privilege access
OpenID Connect AWS IAM integration enables precise control over what actions your GitHub workflows can perform. Instead of broad permissions that traditional access keys might require, you can create highly specific IAM policies attached to your roles. These policies can restrict actions based on specific AWS services, resources, or even time-based conditions.
You can implement least privilege access by:
- Limiting permissions to only the AWS services your workflow actually needs
- Restricting actions to specific resource ARNs or resource patterns
- Adding condition statements that enforce additional security requirements
- Using permission boundaries to set maximum allowed permissions
This granular control means your GitHub Actions secure deployment processes operate with exactly the permissions they need and nothing more.
Role assumption process and security boundaries
The role assumption process creates clear security boundaries between your GitHub repository and AWS resources. When your workflow runs, GitHub generates a JWT (JSON Web Token) containing claims about the workflow context – repository name, branch, actor, and other metadata. AWS validates this token against the trust policy you’ve configured for your IAM role.
The trust policy acts as a gatekeeper, specifying which GitHub repositories, branches, or even specific workflow runs can assume the role. You can configure conditions that only allow:
- Specific repositories or organizations to assume the role
- Certain branches (like
mainorproduction) to trigger deployments - Workflows initiated by particular users or teams
- Actions occurring during specific time windows
This multi-layered security model ensures that even if someone gains unauthorized access to your GitHub repository, they cannot automatically access your AWS resources without meeting all the specified conditions in your trust policy.
Setting Up GitHub Actions OIDC Provider in AWS
Creating the OIDC identity provider in IAM console
Setting up GitHub Actions OIDC AWS authentication starts with creating an identity provider in your AWS IAM console. Navigate to the IAM dashboard and select “Identity providers” from the left sidebar. Click “Create provider” and choose “OpenID Connect” as your provider type.
For the provider URL, enter https://token.actions.githubusercontent.com – this is GitHub’s standardized OIDC endpoint that handles authentication tokens for all GitHub Actions workflows. This URL serves as the foundation for establishing trust between GitHub Actions and your AWS account.
When configuring the audience field, add sts.amazonaws.com as the primary audience. This tells AWS that tokens from GitHub Actions are intended for the Security Token Service, which handles temporary credential generation. You can also add your AWS account ID as an additional audience for extra specificity, though the STS audience typically covers most use cases.
The provider creation process requires you to specify these details upfront, but you can always modify the configuration later through the IAM console if your requirements change.
Configuring thumbprint and audience values correctly
AWS requires a thumbprint verification to ensure the OIDC provider’s authenticity. The thumbprint for GitHub Actions OIDC provider AWS setup is 6938fd4d98bab03faadb97b34396831e3780aea1. This value represents GitHub’s root certificate authority and rarely changes, but AWS occasionally updates their requirements.
To add the thumbprint, you’ll find this option during the provider creation process or by editing an existing provider. Paste the thumbprint value exactly as provided – any typos will cause authentication failures. Some administrators prefer to verify the current thumbprint by checking GitHub’s documentation or using OpenSSL commands, but the standard thumbprint works for most implementations.
The audience configuration deserves special attention because it determines which workflows can assume your IAM roles. Using sts.amazonaws.com provides broad compatibility with GitHub Actions AWS authentication workflows, while more specific audience values offer tighter security controls. You can configure multiple audiences if your organization needs different access patterns for various repositories or workflows.
Establishing trust between GitHub and your AWS account
Once your OIDC identity provider exists, you need to create trust relationships that allow specific GitHub repositories to assume AWS IAM roles. This involves crafting trust policies that specify exactly which GitHub Actions workflows can access your AWS resources.
The trust policy uses conditions to validate incoming tokens against repository names, branches, and other GitHub-specific claims. A typical trust policy includes conditions like token.actions.githubusercontent.com:sub to specify the exact repository and branch combination that can assume the role. You can also use wildcard patterns to allow entire organizations or multiple repositories to use the same role.
GitHub Actions OIDC configuration requires careful attention to the subject claim format. The subject claim follows the pattern repo:OWNER/REPOSITORY:ref:refs/heads/BRANCH for branch-based workflows, or includes additional information for pull requests and tags. Understanding this format helps you write precise trust policies that grant access only to legitimate workflow executions.
Your trust policy should also include the federated principal that references your newly created OIDC provider. This connection tells AWS which identity provider issued the tokens your workflows present. The combination of the federated principal and conditional statements creates a secure authentication pipeline that eliminates the need for long-lived AWS credentials in your GitHub repositories.
Testing your GitHub Actions AWS IAM roles integration involves running a simple workflow that attempts to assume the configured role. Start with basic AWS CLI commands like listing S3 buckets or describing EC2 instances to verify the authentication works correctly before implementing more complex deployment workflows.
Creating and Configuring IAM Roles for GitHub Actions

Defining trust policies for specific repositories
Trust policies act as the gatekeeper for your GitHub Actions OIDC AWS integration, determining which repositories can assume your IAM roles. The key lies in crafting precise trust relationships that prevent unauthorized access while enabling legitimate workflows.
Start by creating a trust policy that validates the GitHub Actions OIDC provider. The Principal field should reference your GitHub OIDC provider ARN, while the Action specifies sts:AssumeRoleWithWebIdentity. The magic happens in the condition block where you define which repositories can use this role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::ACCOUNT-ID:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"token.actions.githubusercontent.com:sub": "repo:your-org/your-repo:ref:refs/heads/main",
"token.actions.githubusercontent.com:aud": "sts.amazonaws.com"
}
}
}
]
}
Setting up condition keys for enhanced security
GitHub Actions AWS authentication becomes bulletproof when you leverage OIDC condition keys effectively. These keys provide granular control over when and how role assumption occurs, creating multiple security checkpoints.
The sub claim represents the most critical condition key, containing repository and branch information. You can restrict access to specific branches using patterns like repo:your-org/your-repo:ref:refs/heads/main for main branch only, or repo:your-org/your-repo:* for all branches and tags.
Repository-level restrictions use the repository claim: token.actions.githubusercontent.com:repository equals your-org/your-repo. For organization-wide access, the repository_owner claim works well: token.actions.githubusercontent.com:repository_owner equals your-org.
Environment-based conditions add another security layer. When using GitHub environments, include token.actions.githubusercontent.com:environment equals production to ensure only production deployments can assume sensitive roles.
Actor-based restrictions prevent unauthorized users from triggering workflows: token.actions.githubusercontent.com:actor equals specific-username or use token.actions.githubusercontent.com:actor_id for numeric user IDs.
Attaching appropriate permission policies
Permission policies define what your GitHub Actions workflows can actually do in AWS once they assume the IAM role. The principle of least privilege should guide every policy attachment decision.
Create custom policies tailored to your specific GitHub Actions AWS IAM roles requirements rather than using broad AWS managed policies. For deployment workflows, you might need permissions for S3 bucket operations, CloudFormation stack management, or ECS service updates.
Example deployment policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource": "arn:aws:s3:::your-deployment-bucket/*"
},
{
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:UpdateStack",
"cloudformation:DescribeStacks"
],
"Resource": "arn:aws:cloudformation:region:account:stack/your-stack/*"
}
]
}
Consider time-based restrictions for sensitive operations. Session duration limits in the role’s maximum session duration setting prevent long-running token abuse.
Testing role assumption capabilities
Testing your GitHub Actions OIDC configuration prevents deployment failures and security gaps. Start with a simple workflow that attempts role assumption without performing actual operations.
Create a test workflow file:
name: Test OIDC Role Assumption
on: workflow_dispatch
permissions:
id-token: write
contents: read
jobs:
test-role:
runs-on: ubuntu-latest
steps:
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v2
with:
role-to-assume: arn:aws:iam::ACCOUNT-ID:role/your-role-name
aws-region: us-east-1
- name: Test AWS access
run: aws sts get-caller-identity
Monitor CloudTrail logs during testing to verify the assume role events appear correctly. Check for any access denied errors and validate that the assumed role identity matches expectations.
Test different scenarios: various branches, pull requests from forks, and different repository contributors. Each test reveals potential security gaps or overly restrictive conditions.
Use AWS CloudWatch to set up alerts for unusual role assumption patterns, helping detect potential security breaches or misconfigurations in your GitHub Actions secure deployment setup.
Implementing OIDC Authentication in GitHub Workflows

Configuring workflow permissions for token requests
Your GitHub workflow needs specific permissions to request OIDC tokens for AWS authentication. The id-token permission is crucial – without it, your workflow can’t generate the JWT tokens required for OIDC authentication with AWS IAM roles.
Set permissions at the workflow level or job level:
permissions:
id-token: write # Required for OIDC token requests
contents: read # Standard permission for repository access
The id-token: write permission allows GitHub Actions to generate JWT tokens containing claims about your workflow run. These tokens include repository information, branch details, and workflow context that AWS uses to verify the authenticity of your requests.
For enhanced security, apply permissions at the job level rather than workflow level when dealing with multiple jobs that have different requirements. This follows the principle of least privilege and reduces potential attack surfaces.
Using the official configure-aws-credentials action
The configure-aws-credentials action handles the complex OIDC authentication process seamlessly. This official AWS action manages token exchange, credential retrieval, and environment variable setup automatically.
Basic configuration looks like this:
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v4
with:
role-to-assume: arn:aws:iam::123456789012:role/GitHubActionsRole
role-session-name: MyGitHubAction
aws-region: us-east-1
The action supports multiple authentication methods, but when using GitHub Actions OIDC AWS integration, you only need the role ARN. The action automatically detects the OIDC environment and uses GitHub’s JWT token for authentication.
You can also specify additional parameters:
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v4
with:
role-to-assume: arn:aws:iam::123456789012:role/GitHubActionsRole
role-session-name: $.name }}-${{ github.run_id }}
aws-region: us-east-1
role-duration-seconds: 3600
role-skip-session-tagging: true
Retrieving and using temporary AWS credentials
After successful OIDC authentication, AWS provides temporary credentials that your workflow can use for subsequent AWS API calls. The configure-aws-credentials action automatically sets these credentials as environment variables:
AWS_ACCESS_KEY_IDAWS_SECRET_ACCESS_KEYAWS_SESSION_TOKENAWS_DEFAULT_REGION
Your workflow steps can now use any AWS CLI commands or SDK calls without additional authentication:
- name: List S3 buckets
run: aws s3 ls
- name: Deploy to Lambda
run: |
aws lambda update-function-code \
--function-name my-function \
--zip-file fileb://deployment.zip
The temporary credentials typically last 1-12 hours depending on your IAM role configuration. AWS automatically handles credential rotation, so your workflows don’t need to manage token refresh cycles.
For debugging purposes, you can verify credential retrieval without exposing sensitive information:
- name: Verify AWS identity
run: aws sts get-caller-identity
Best practices for workflow security
GitHub Actions AWS authentication requires careful security considerations. Always use dedicated IAM roles for GitHub Actions rather than sharing roles with other services. This isolation makes it easier to audit permissions and rotate credentials when needed.
Pin action versions to specific releases rather than using @main or @master tags. This prevents supply chain attacks where malicious code could be injected into action updates:
uses: aws-actions/configure-aws-credentials@v4.0.1 # Pinned version
Store sensitive configuration like account IDs and role ARNs in GitHub repository secrets or environment-level secrets. This keeps sensitive information out of your workflow files and git history:
role-to-assume: $_ROLE_ARN }}
Implement conditional logic to prevent accidental deployments from feature branches. Use GitHub’s context information to restrict AWS access to specific branches:
- name: Configure AWS credentials
if: github.ref == 'refs/heads/main'
uses: aws-actions/configure-aws-credentials@v4
with:
role-to-assume: $ARN }}
Regular security audits should review IAM role permissions and GitHub Actions OIDC configuration. Remove unused permissions and validate that trust policies match your current repository structure and workflow requirements.
Consider using different IAM roles for different environments (development, staging, production) and configure branch-based conditional logic to ensure workflows assume appropriate roles based on the deployment target.
Troubleshooting Common OIDC Integration Issues

Resolving Trust Policy Configuration Errors
Trust policy misconfigurations represent the most frequent roadblock when setting up GitHub Actions OIDC AWS authentication. The trust policy acts as the gatekeeper, determining whether GitHub Actions can assume your IAM role.
Common trust policy errors include incorrect condition blocks that don’t match your repository structure. When your condition specifies "StringEquals": { "token.actions.githubusercontent.com:sub": "repo:myorg/myrepo:ref:refs/heads/main" } but your workflow runs from a different branch or uses pull requests, authentication fails silently.
Check your audience configuration carefully. The default audience should be "token.actions.githubusercontent.com:aud": "sts.amazonaws.com", but many developers accidentally modify this value or add extra audiences that break the validation process.
Repository naming inconsistencies cause authentication failures too. Double-check that your trust policy exactly matches your GitHub repository path, including proper capitalization. GitHub Actions OIDC configuration is case-sensitive, and MyRepo differs from myrepo in the condition evaluation.
Wildcard usage in trust policies requires special attention. While "StringLike": { "token.actions.githubusercontent.com:sub": "repo:myorg/*" } seems convenient, it can create security vulnerabilities by allowing access from unintended repositories within your organization.
Fixing Token Validation and Audience Mismatches
Token validation errors typically surface as “AssumeRoleWithWebIdentity” failures in your GitHub Actions logs. These errors stem from mismatched token claims or incorrect OIDC provider configuration.
Start by examining the token claims your workflow receives. Add a debug step to your workflow that prints the JWT token claims:
- name: Debug OIDC Token
run: |
echo "Token subject: ${{ github.token }}"
echo "Repository: ${{ github.repository }}"
echo "Ref: ${{ github.ref }}"
Audience mismatches occur when your IAM role expects a different audience than what GitHub Actions provides. The standard audience for GitHub Actions AWS authentication is sts.amazonaws.com. If you’ve customized this value in your workflow using the audience parameter, ensure it matches your trust policy exactly.
Time synchronization issues can cause token validation failures. GitHub’s tokens have short expiration windows, and clock skew between GitHub’s servers and AWS can reject valid tokens. This problem usually resolves automatically, but persistent issues might indicate broader infrastructure problems.
Token format changes in GitHub Actions occasionally break existing configurations. GitHub periodically updates their JWT token structure, adding or modifying claims. Review GitHub’s changelog and update your trust policies to accommodate new token formats when experiencing sudden authentication failures.
Debugging Permission Denied Scenarios
Permission denied errors in GitHub Actions AWS IAM roles integration often mask the actual root cause. These errors can stem from trust policy issues, insufficient IAM permissions, or misconfigured OIDC providers.
Start debugging by checking your CloudTrail logs for detailed error messages. CloudTrail provides complete context about failed AssumeRoleWithWebIdentity calls, including which condition in your trust policy caused the rejection.
Role permission boundaries frequently cause confusion. Even when your role has the necessary policies attached, permission boundaries can block specific actions. Verify that your role doesn’t have restrictive permission boundaries that conflict with your GitHub workflows’ requirements.
Cross-account scenarios introduce additional complexity. When your GitHub Actions workflow needs to assume roles in different AWS accounts, ensure each account’s OIDC provider configuration matches exactly. Inconsistent thumbprints or provider URLs between accounts cause authentication failures.
Session duration limits can trigger permission denied errors for long-running workflows. The default session duration might be insufficient for complex deployment processes. Increase the maximum session duration in your IAM role configuration to accommodate longer workflows.
Resource-based policies on target AWS services sometimes conflict with your IAM role permissions. S3 bucket policies, KMS key policies, and other resource-based restrictions can override your role’s permissions, causing unexpected access denials even when your role appears correctly configured.
Enable detailed CloudTrail logging and examine the specific AWS API calls your GitHub Actions workflow makes. This approach reveals exactly which permissions are missing and helps distinguish between authentication failures and authorization problems.

GitHub Actions OIDC with AWS IAM Roles gives you a rock-solid way to connect your workflows to AWS without juggling long-lived access keys. You get the security benefits of temporary credentials that AWS generates on the fly, plus fine-grained control over what your workflows can actually do in your AWS account. Setting up the OIDC provider and configuring your IAM roles might feel like a lot at first, but once you get it running, you’ll never want to go back to storing static credentials.
The best part? You can sleep better knowing your CI/CD pipeline follows security best practices without making your life harder. Start with a simple workflow and one IAM role, then expand from there as you get comfortable with the setup. Your future self will thank you for making this switch, and your security team will definitely appreciate the upgrade.